Configure SSO with Okta Authorization
If you manage your enterprise accounts using Okta, you can choose Okta as the authorization server for EMQX Cloud and enable Single Sign-On (SSO). Additionally, you need to configure OpenID Connect (OIDC) settings in Okta. This page provides examples of OIDC configurations in both EMQX and Okta to help you understand the end-to-end configuration process for connecting an Enterprise Identity Provider (IdP) with EMQX Cloud to enable SSO.
Prerequisites
- An EMQX Cloud Root account.
- An administrator account for Okta Workforce Identity.
- Be familiarity with Okta's enterprise account management. Refer to Okta documentation for guidance.
Step 1: Enable SSO in EMQX Cloud
Log in to Cloud Console using your EMQX Cloud Root account.
Click Settings from the left menu, and select the Single Sign-On tab.
Click Enable SSO to enter the SSO configuration flow.
Select Okta as the OIDC Identity Provider and click Next.
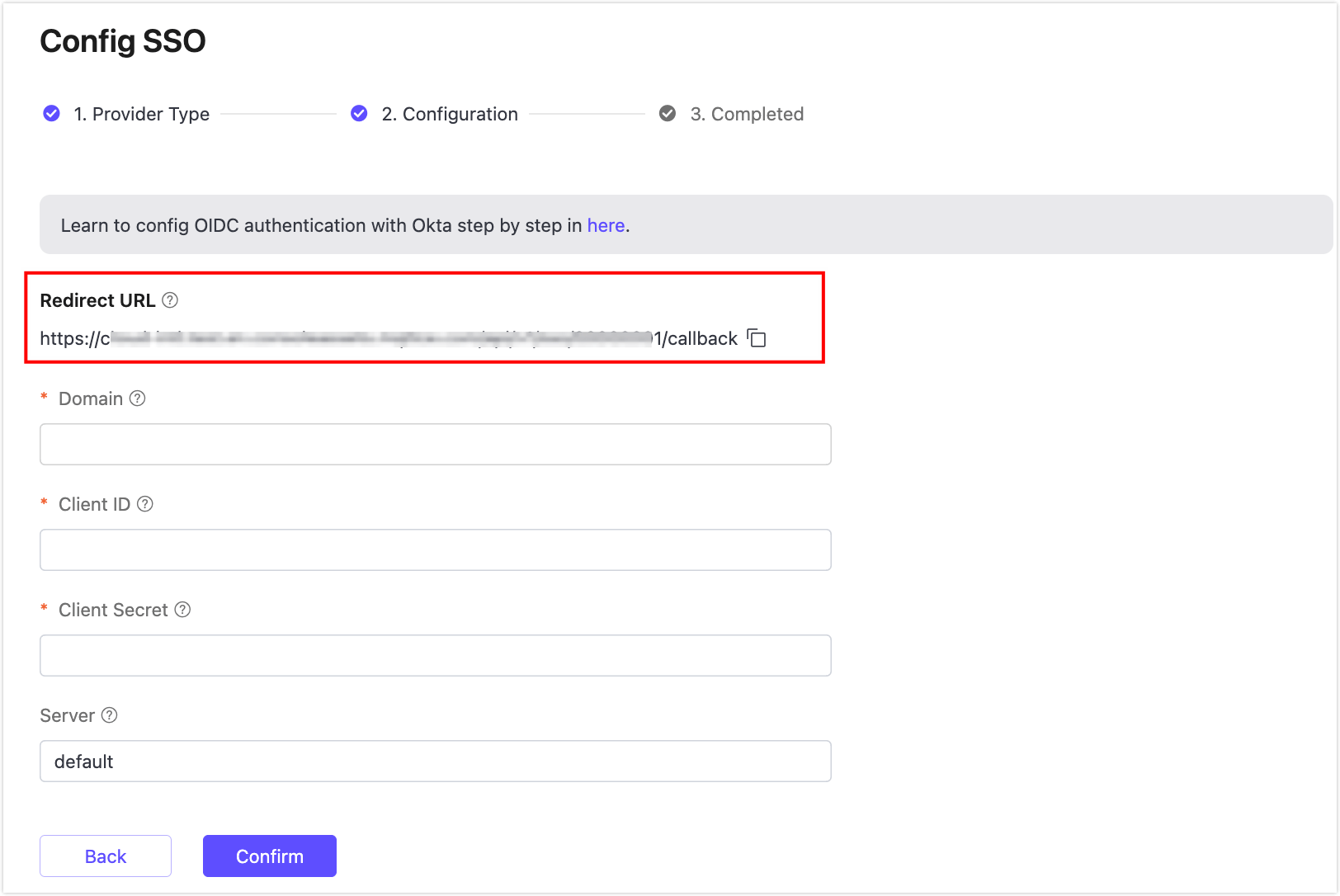
You can now view the Redirect URL on the page; this address will be used in the subsequent configuration.
Step 2: Create an Application in Okta
Log in to Okta Workforce Identity using your administrator account.
TIP
You may need to click the Admin button to access the administrator interface.
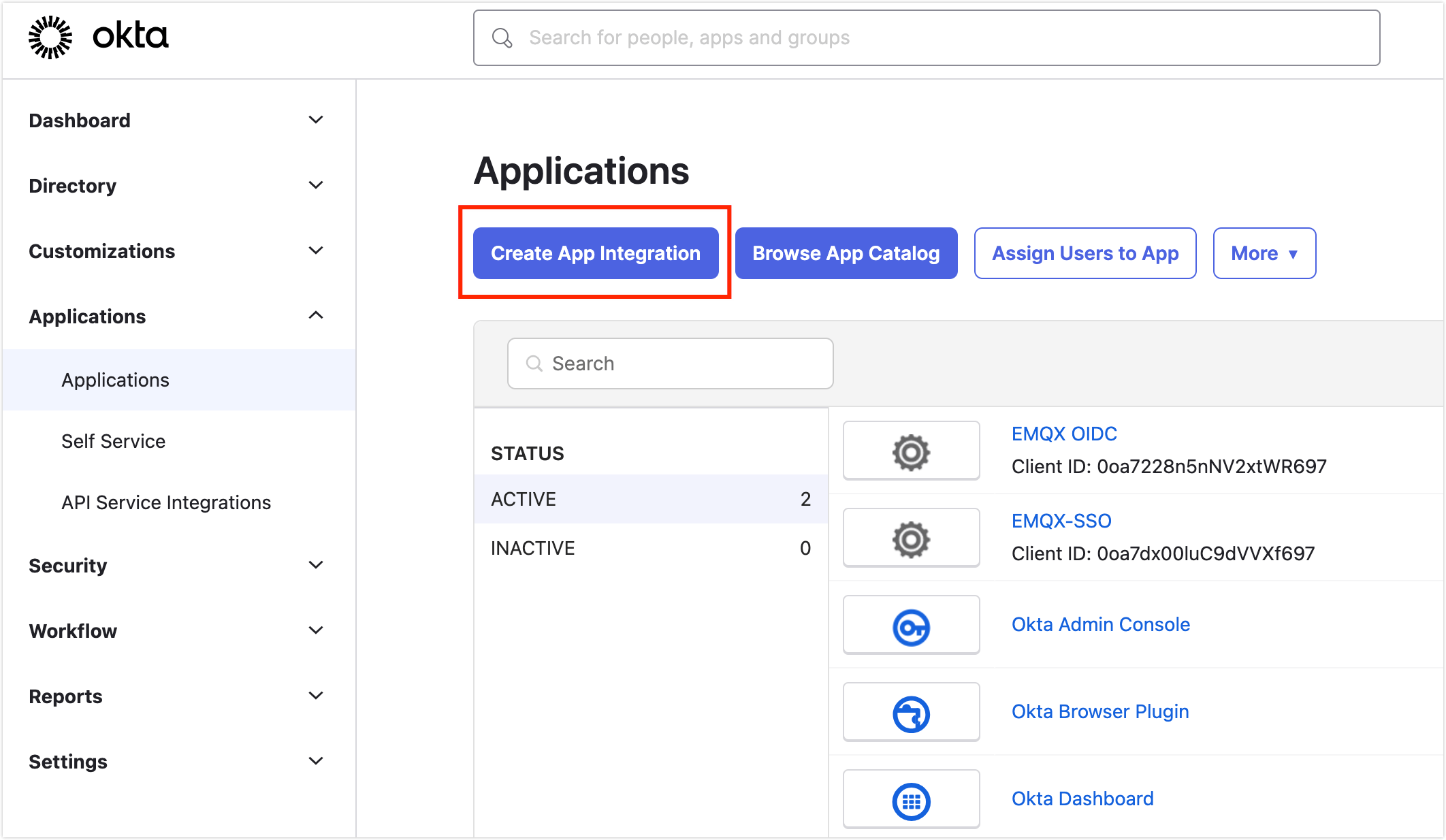
In the administrator interface, go to Applications -> Applications in the left menu.
Click Create App Integration on the main page.
In the pop-up, choose OIDC - OpenID Connect as the Sign-in method, and select Web Application as the Application type, then click Next to enter the configuration page.
In the New Web App Integration configuration page, fill in the following configuration information:
- App integration name: Enter the app name, for example,
EMQX-SSO. - Sign-in redirect URIs: Enter the redirect URL from step 1.
- Controlled access: You can fill this in based on your requirements; in this example, select
Skip group assignment for now.
- App integration name: Enter the app name, for example,
After completing the configuration, click Save to access the General page of the created application.
Step 3: Configure SSO Information in EMQX Cloud
Go to the Config SSO page in EMQX Cloud and follow these steps:
On the Config SSO page in EMQX Cloud, configure the following information:
- Domain: Enter
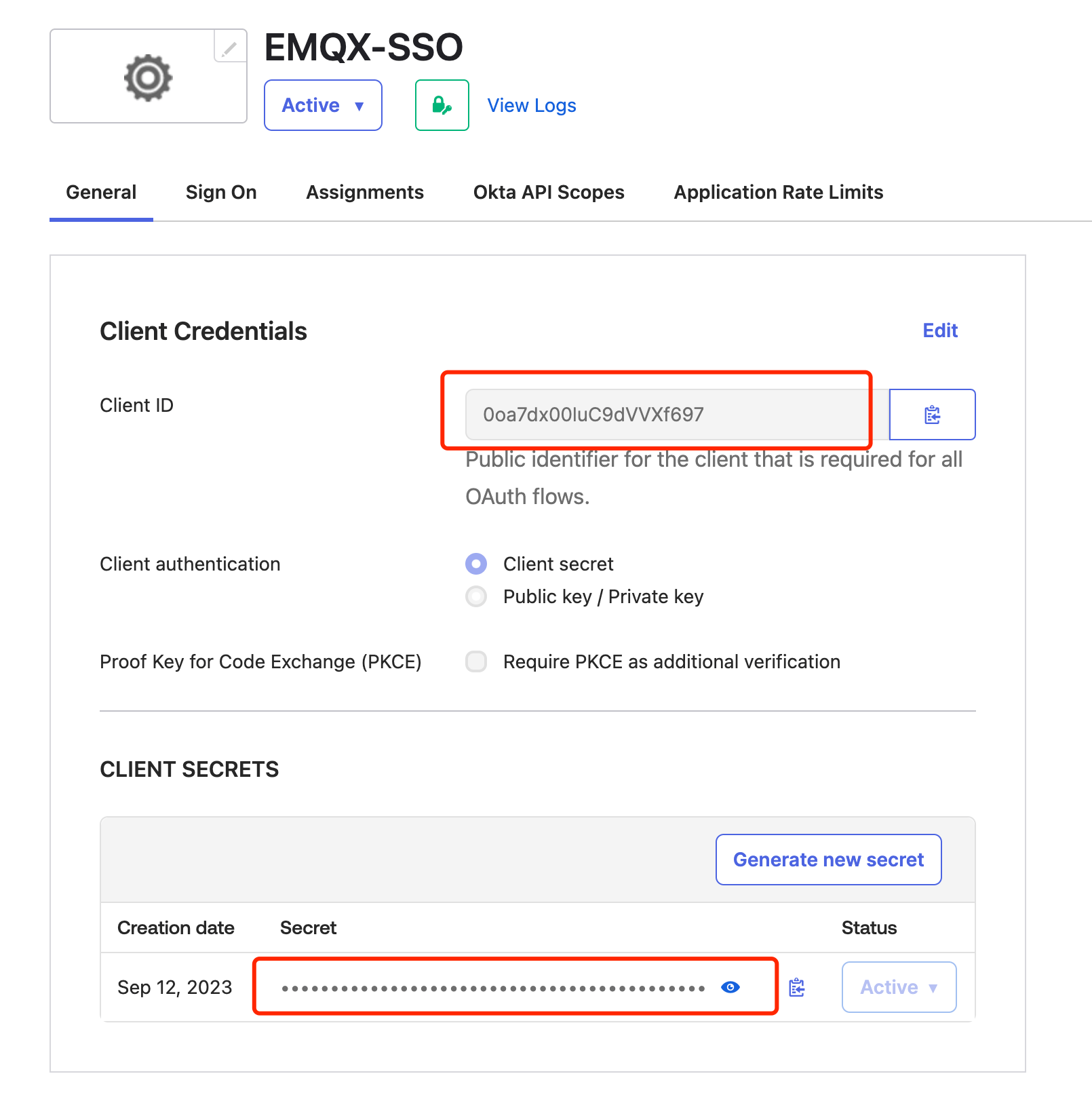
trial-9021952.okta.comas the Okta domain. The Domain field format is{YourOktasubdomain}.okta.com. - Client ID: Enter the Client ID obtained from the Okta application overview page.
- Client Secret: Enter the Client Secret obtained from the Okta application overview page.
- Server: If you don't have your own authentication server, it defaults to
default. If you have your own authentication server, please enterauthorizationServerId. For more Okta authentication settings, refer to the relevant documentation.
- Domain: Enter
Click Confirm to complete the configuration.
If configured successfully, you will reach a page confirming that SSO has been successfully enabled, and you will get the SSO login URL.
Step 4: Add Users and Authorize the Application in Okta
In the Okta administrator interface, select Directory -> People from the left menu.
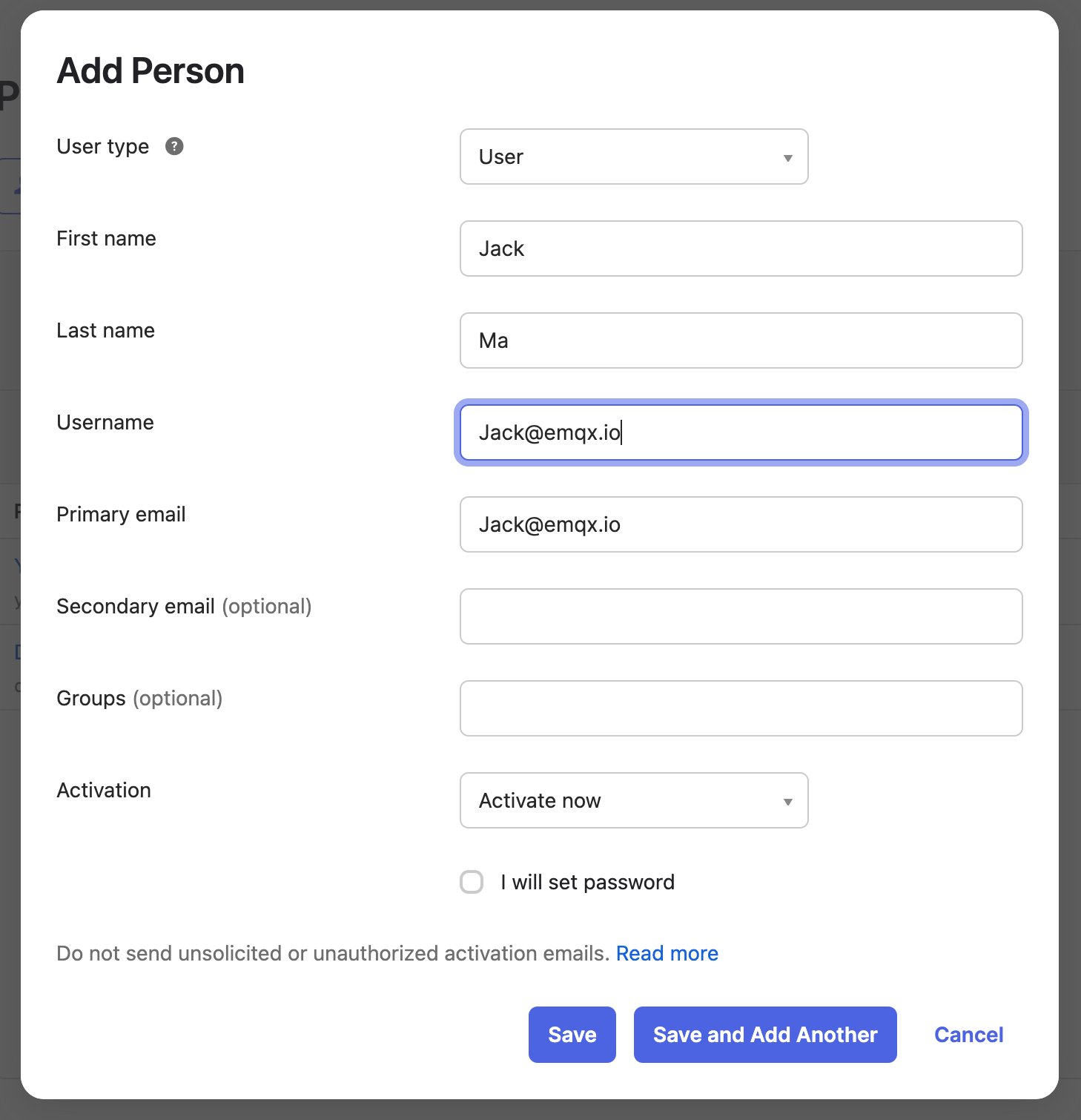
Click Add Person on the main page.
Fill in user information, such as Jack@emqx.io. You can also authorize user groups.
Click Save to return to the People page.
Click the user's name to access their user information, then click Assign Applications to authorize the
EMQX-SSOapplication created in step 2. Click Assign and provide additional user information as needed, then click Save and Go Back.You can see that the application has been authorized (Assigned). Click Done to complete the application authorization for the user.
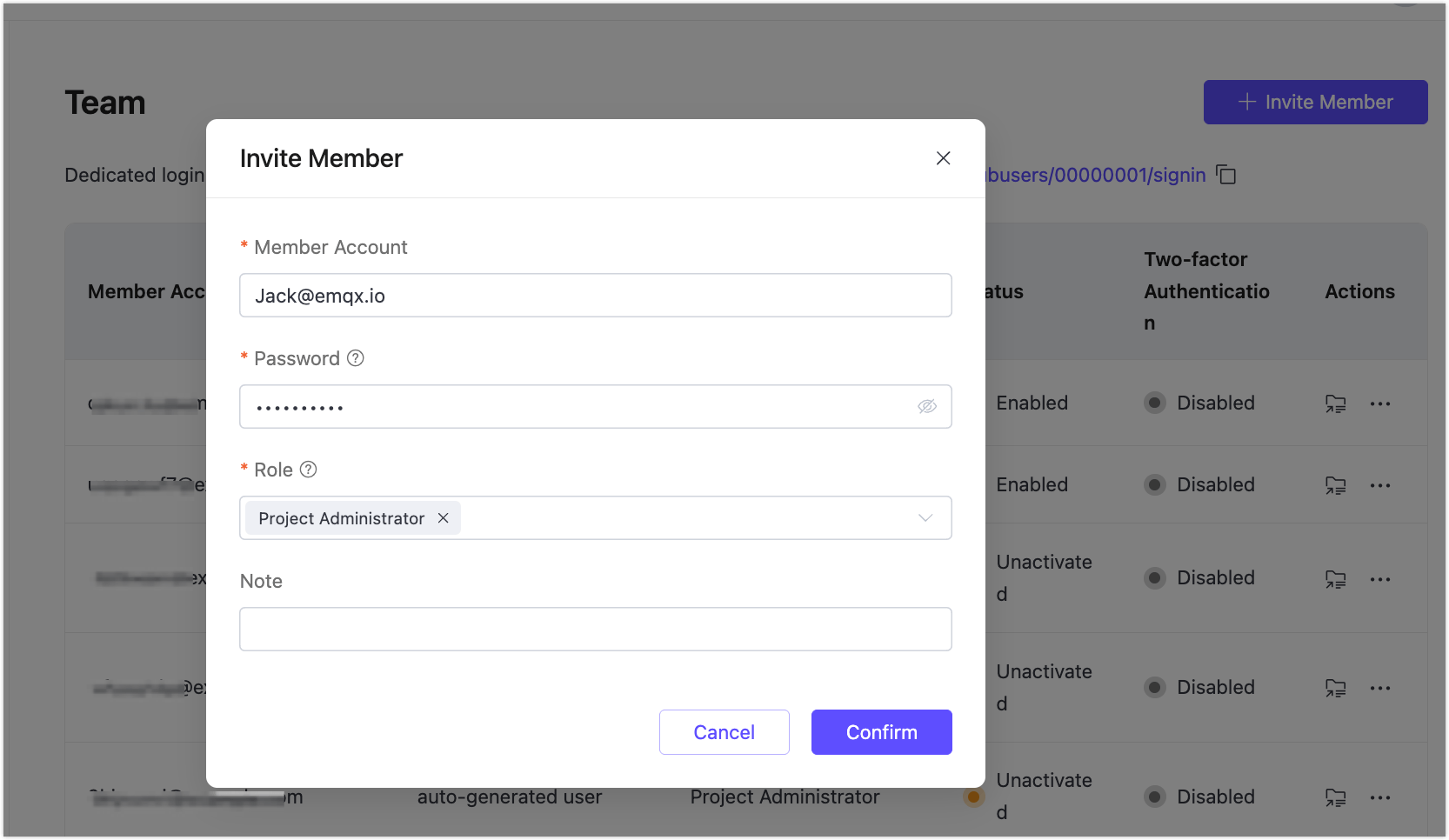
Step 5: Create a Member Account in EMQX Cloud
In the Platform Console, click Team from the left menu.
Click + Invite Member in the upper right corner.
In the Invite Member pop-up, enter the same email account that was authorized in Azure AD: Jack@emqx.io. Assign a role to this account. Refer to Roles and Permissions for setting different roles.
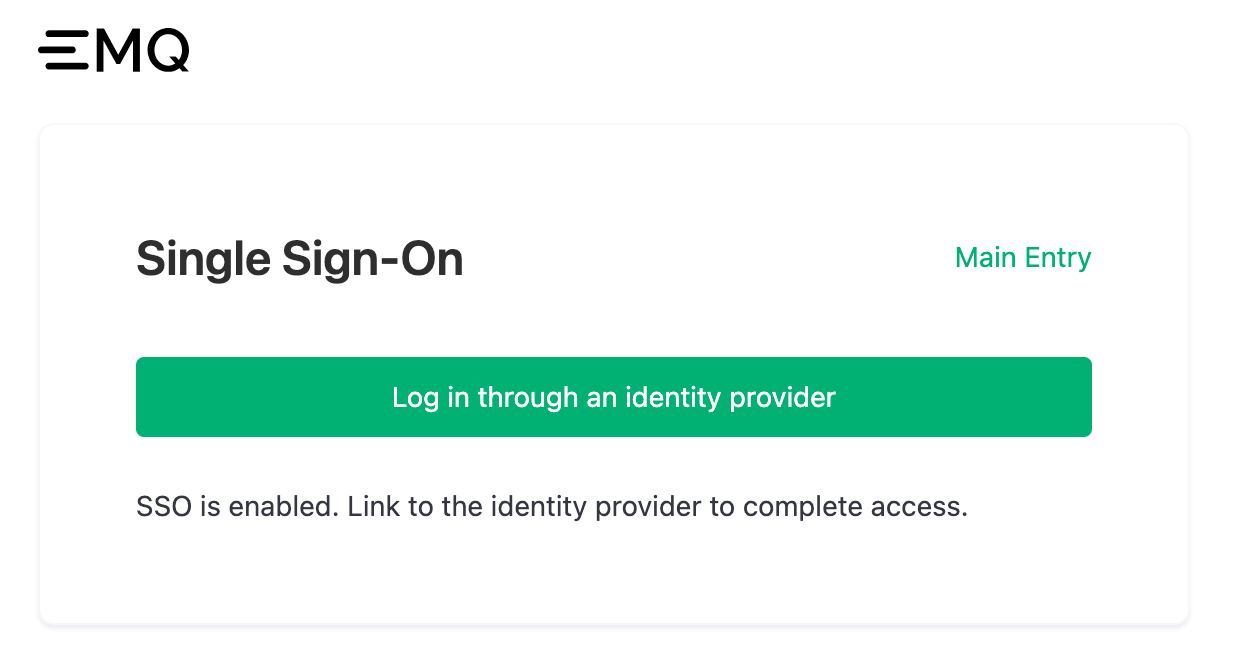
Open the dedicated URL for team members shown on the Teams page. Click Log in through an identity provider, and the browser will redirect to the Okta login page.
Complete the login process on the Okta login page, and the browser will automatically return to the EMQX Cloud to complete the SSO login.